Managed Technology Services: Why Managing Your Own IT Infrastructure Is Holding Your Business Back

Before you start reading ... want to save a PDF version of this post for later?
Just enter your email below and we'll send you a copy.
Managed Technology Services: Why Managing Your Own IT Infrastructure Is Holding Your Business Back
If there’s one thing that all businesses can agree upon it’s that time equals money.
It’s the reason why organisations large and small all over the globe are on the constant lookout for ways to boost productivity and performance – all while maximising resources and lowering costs.
And this holds especially true when it comes to your IT infrastructure – the backbone that keeps your business running smoothly and competitively.
Without fast, agile, flexible and scalable IT – not to mention the security and backup provisions that must be part of it – you stand next to zero chance of gaining competitive advantage in the long term, let alone stabilizing growth and success in the short term.
This is where zsah's managed services come in.
Why Waste Time Managing Infrastructure?
Despite its great importance, it’s frequently impossible to sustain an in-house IT department dedicated to ensuring the smooth running of your systems and infrastructure without losing focus on doing what you do best – growing your business and winning new customers.
The fact of the matter is that the core technology that today’s businesses rely upon is not infallible.
Hardware failures and network downtime are unfortunately common occurrences that require all hands on deck to get your systems back up and running again.
And while your internal IT staff are busy putting out fires, they’re not focussing on more strategic projects.
With IT managed services, all of your technology headaches can disappear overnight.
By bridging the gap between the capabilities of your internal IT department and the demand for high-performance technology, managed IT service providers improve the day-to-day running of your business, ensuring hardware is always working to its optimum, applications are constantly available to employees and customers, security is ensured, and downtime is kept to an absolute minimum.
So, who’s using managed technology services?
Larger Enterprises More Likely to Use Managed Technology Services
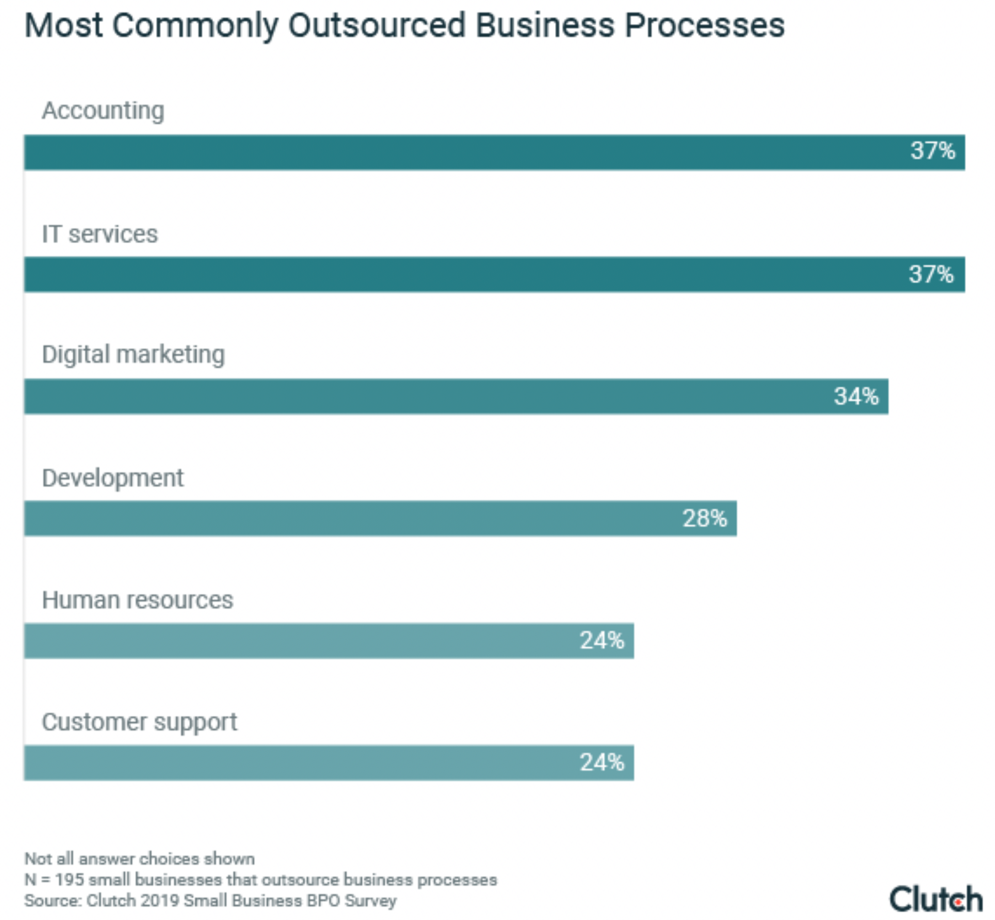
Though managed technology services have existed for years, many small organisations still rely solely upon in-house IT teams to manage their technology. According to recent research from Clutch, only 37% of small businesses currently outsource IT projects.
(Image source: clutch.co)
Larger enterprises, meanwhile, are much more likely to outsource their IT. In fact, it is estimated that 90% of Fortune 1000 companies use managed technology services providers to provide at least part of the IT infrastructure or services.
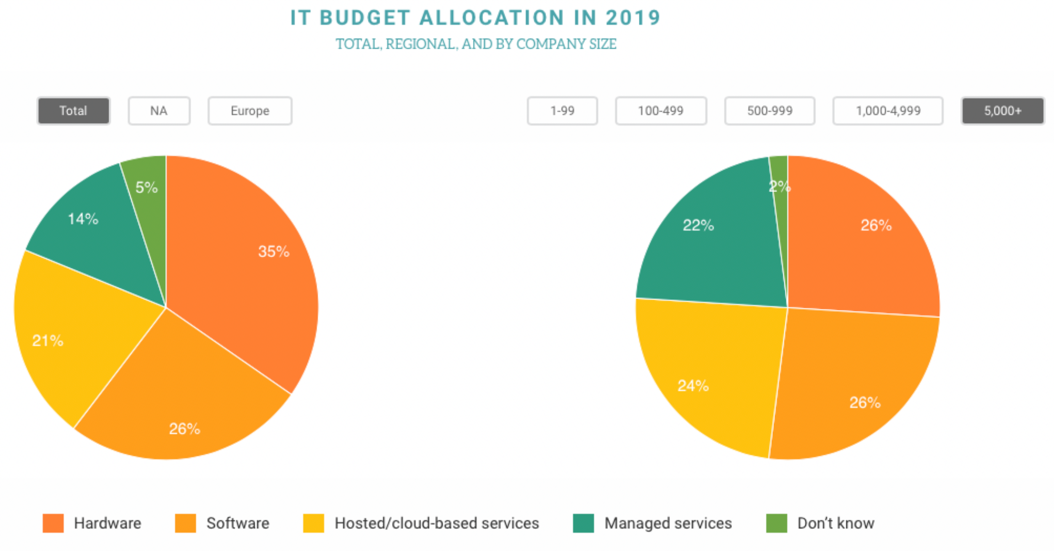
Further research from Spiceworks confirms that – generally – as a percentage of total IT spend, managed services budget allocations get larger as company size increases.
Just 9% of IT budgets get spent on managed services at companies with 1-99 employees. However, this rises to 12% at companies with 100-499 employees, 20% at companies with 500-999, dips slightly to 17% at companies with 1000-4,999, before rising again to 22% at companies with 5,000+ employees.
(Image source: spiceworks.com)
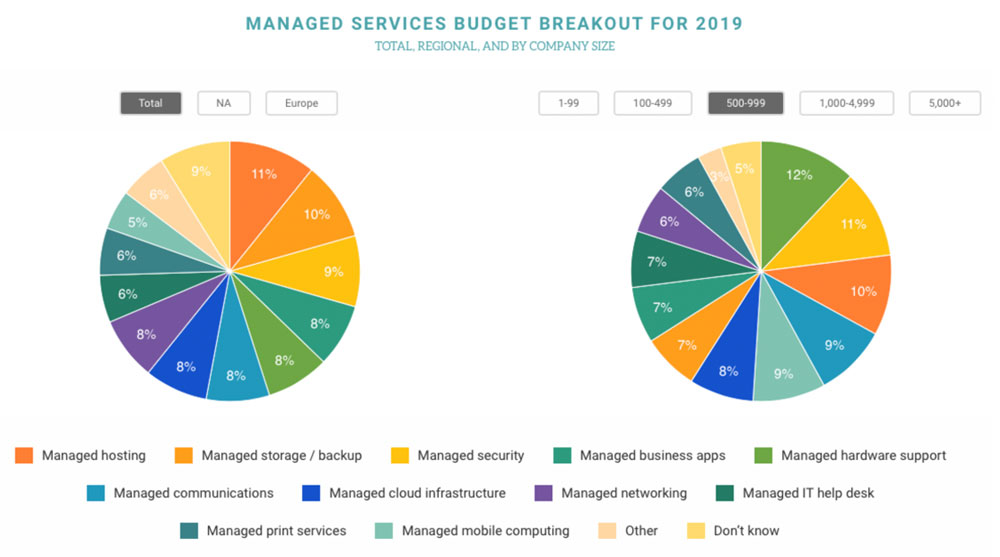
Budget Breakdown
How do managed technology services budgets break down? Well, according to the Spiceworks report – entitled “2019 State of IT” – managed hosting (11%), storage/backup (10%), and security (9%) top the list, with business apps, hardware support, communications, cloud infrastructure and networking all commanding 8% respectively of total managed services budgets.
(Image source: spiceworks.com)
Growing Global Market
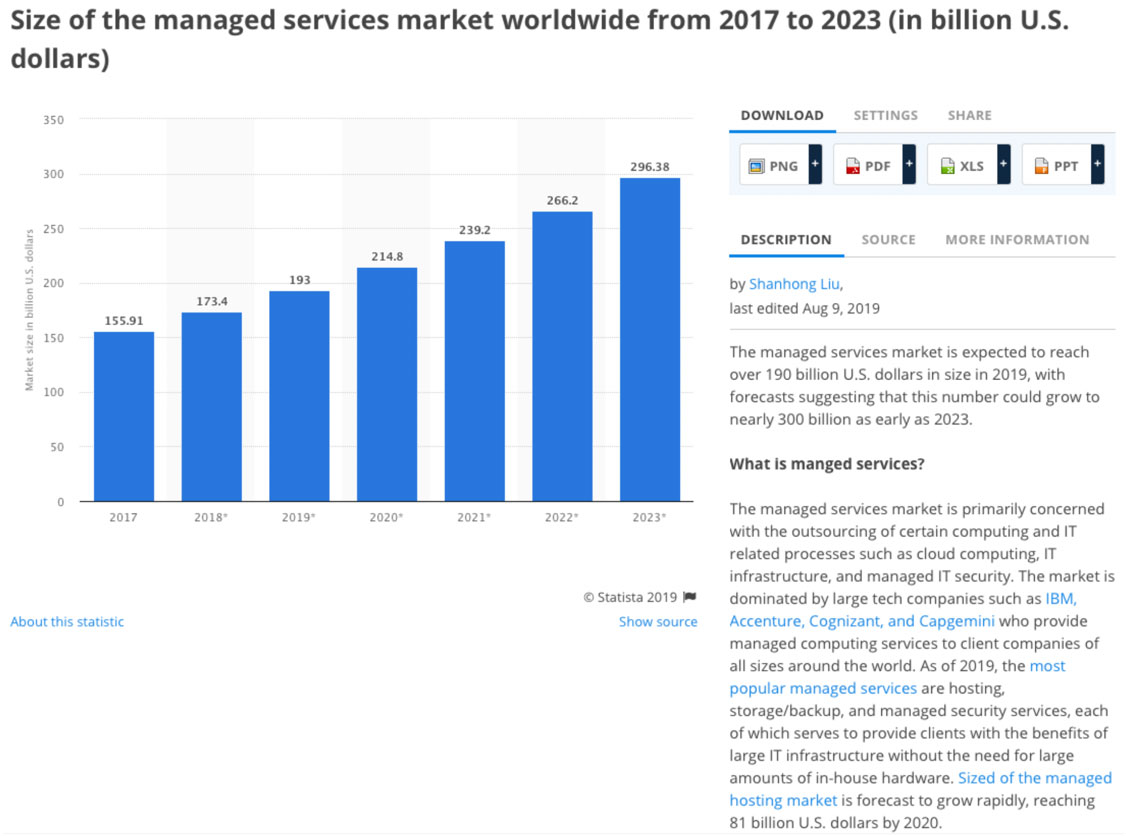
In all, the size of the managed technology services market worldwide is growing as more and more businesses recognise the value of outsourcing IT.
Figures curated by Statista.com place the current global managed services market at USD 193 billion in 2019, with forecasts suggesting that this number could grow to USD 296 billion by 2023.
(Image source: statista.com)
While the precise services various organisations use vary, managed technology services providers are clearly offering a valuable and broad range of computing services that companies of all types and sizes are utilising.
Benefits of Managed Technology Services
Organisations that have yet to harness the power of managed technology services could be holding their business back from growth.
IT plays a crucial role in every aspect of the modern business – from hardware and software to security, cloud, and how communication with both employees and customers is handled.
So, what are the key benefits of utilising managed technology services, and how can they maximise your organisation’s success?
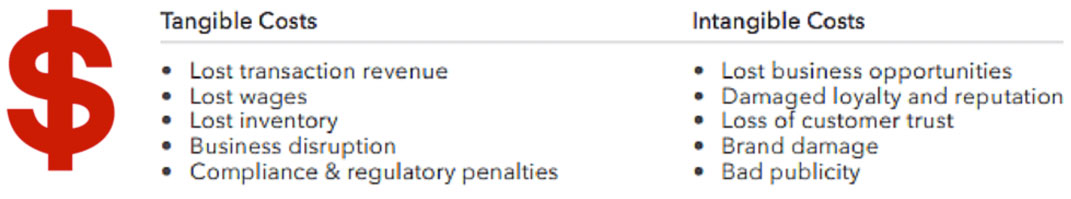
Decreasing Costly Downtime
Downtime costs. Even brief outages can impact a company’s revenue stream and profits. When they happen, outages can impair customer journeys and/or grind in-house productivity across your employee base to a standstill.
When it comes to your customers, depending on the service or application, an outage can affect users who are trying to shop, perform business transactions, or simply get work done.
As such, when your service goes down, it’s not only customer satisfaction that starts to plummet, it’s your company’s bottom line, too.
(Image source: cgsinc.com)
And if it’s not your customers that are directly affected, then it will be your employees. Network failures, application crashes and other IT issues can prevent your employees from working – perhaps for many hours while your stretched in-house IT team struggles to get things back up and running.
Downtime, indeed, is a serious productivity killer.
The Cost of Downtime
There are numerous studies that try to pin down precisely how much downtime costs a business.
According to Gartner, the average cost of downtime is USD 5,600 per minute. That mounts up to an eye-watering USD 336,000 per hour.
In 2017, ITIC sent out an independent survey to measure downtime costs.
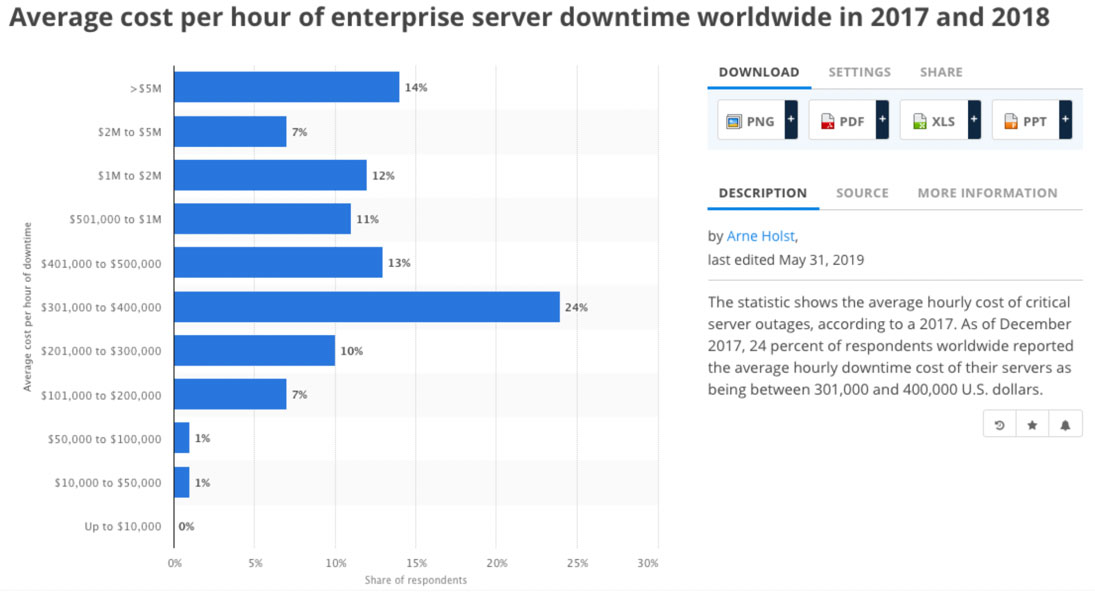
It found that 98% of organisations say that a single hour of downtime costs over USD 100,000, with 81% putting the figure at over USD 300,000. For 33% of businesses, 60 minutes of downtime would cost their firms between USD 1 million and USD 5 million.
Figures from Statista.com reveal 24% of organisations worldwide reporting average hourly downtime costs amounting to between USD 301,000 and USD 400,000, with 14% reporting greater than USD 5 million in costs.
(Image source: statista.com)
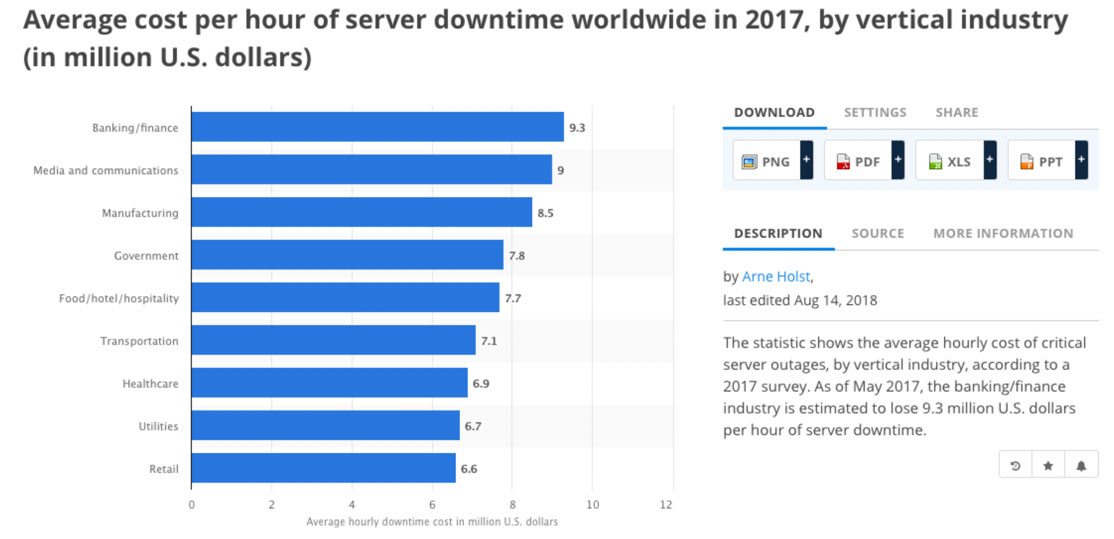
Breaking this down, Statista.com also reveals how the average hourly cost of downtime varies by industry:
(Image source: statista.com)
Elsewhere, IHS Markit surveyed 400 companies and found downtime was costing them a collective USD 700 billion per year – 78% of which was from lost employee productivity during outages.
“Our research found that the cost of ICT downtime is substantial, from USD 1 million a year for a typical mid-size company to over USD 60 million for a large enterprise,”
Said Matthias Machowinski, Directing Analyst for Enterprise Networks and Video at IHS.
“The main cost of downtime is lost productivity and revenue. Fixing the problem is a minor cost factor, which means a small investment in increasing the reliability of ICT systems will provide an outsized return by reducing productivity and revenue losses.”
Ensuring Business Continuity with Managed Technology Services
Though precise estimates vary, the sum of them all is that outages can potentially cost an organisation hundreds of thousands if not millions in lost productivity and revenues.
Waiting around for the next costly outage to happen is simply not an option.
When you work with a managed technology services provider, one of the major benefits is that they will monitor your network and infrastructure 24 hours a day, 365 days of the year.
This means that when there’s a problem, your provider will know about it immediately and will fix it quickly before it results in significant and costly downtime.
And of course, providers don’t just sit around waiting for your systems to fail – they perform regular, proactive maintenance, so the likelihood of running into issues is minimised in the first place.
What’s more, disaster recovery (DR) solutions – which utilise cloud computing to protect applications and data from a natural or human disaster – ensure business continuity via complete recovery from the cloud.
80% of all companies that experience a major interruption of more than five days without any DR plans, go out of business.
(Source: zsah.net)
No matter whether your services and infrastructure are hosted, on-premise or cloud-based, managed technology services providers monitor and pre-empt any potential issues, meaning that you no longer need to even consider – let alone worry about – the looming threat of downtime.
Increased Security
Are your firewalls up to date? Do you regularly audit your workstations and servers? Is all of your customers’ data adequately protected in full compliance with GDPR standards?
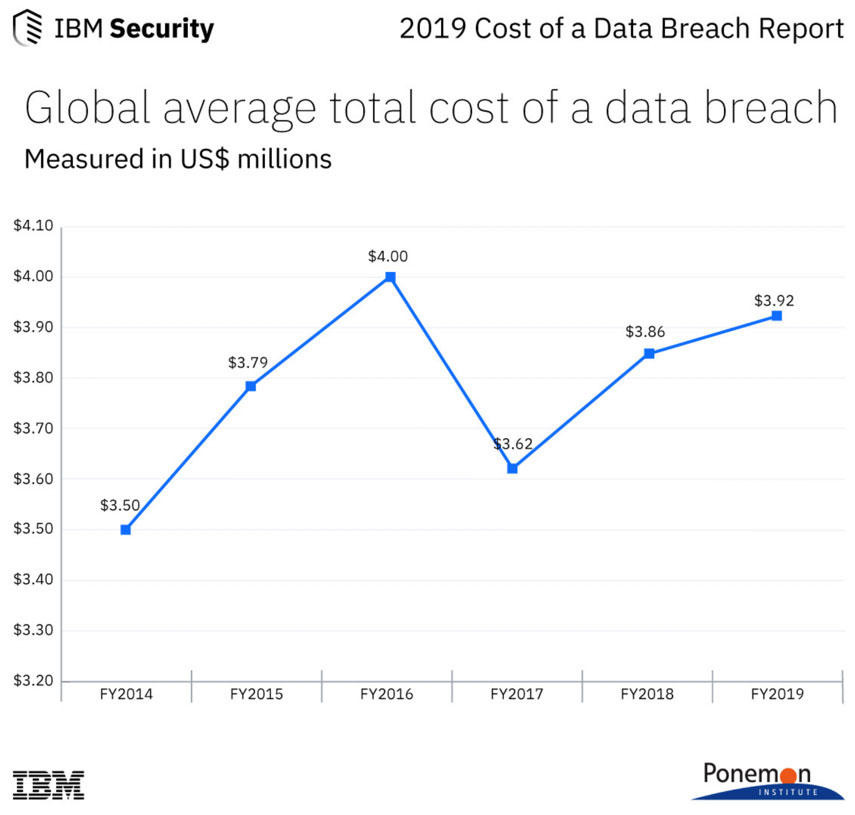
They need to be. According to IBM’s most recent Cost of a Data Breach Report, the global average cost of a data breach for 2019 is USD 3.92 million – a 1.5% increase from last year’s study.
As shown in the following chart, the average total cost of a data breach climbed from USD 3.5 million in 2014, representing a growth of 12% between 2014 and 2019.
(Image source: securityintelligence.com)
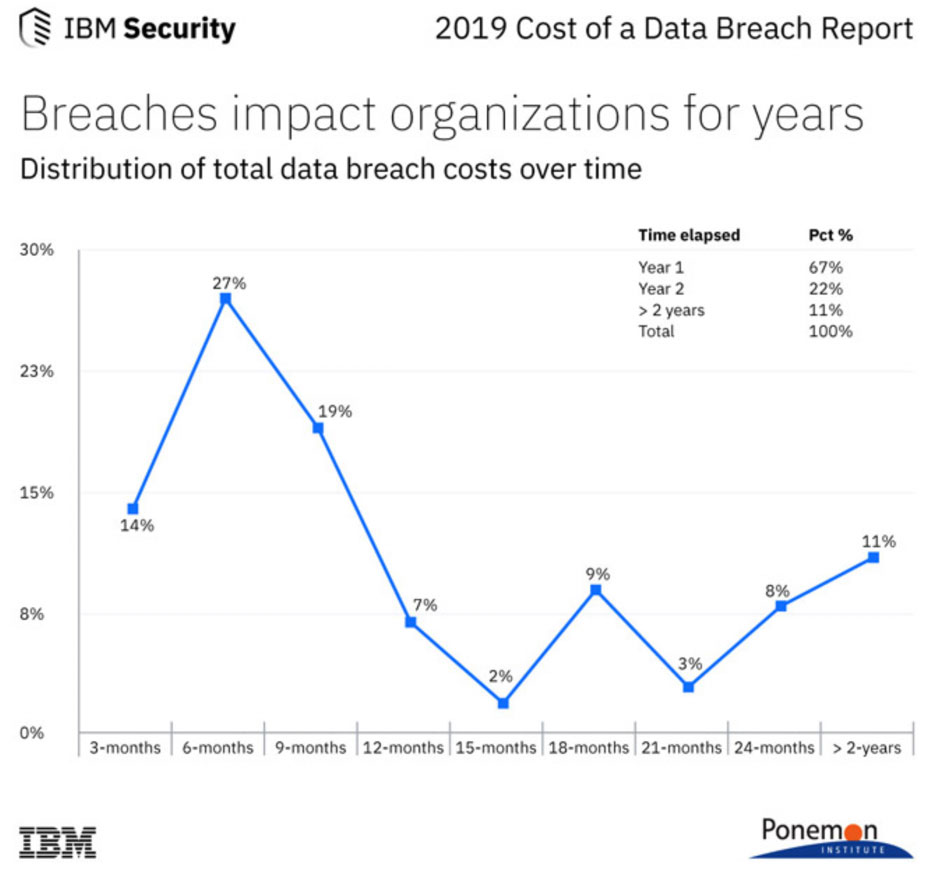
These rising expenses are largely due to the fact that the financial impact of data breaches can last for multiple years.
For the first time in its history, the IBM report examined the longtail financial impact of a data breach, finding that the effects are felt for years.
While an average of 67% of data breach costs are realised within the first year, 22% accrue in the second year, and another 11% more than two years after the initial breach.
(Image source: helpnetsecurity.com)
The analysis takes into account hundreds of cost factors, including legal, regulatory and technical activities, loss of brand equity, customers, and employee productivity.
It also finds that longtail costs are higher in the second and third years for organisations in highly-regulated environments, such as healthcare, financial services, energy and pharmaceuticals.
“Cybercrime represents big money for cybercriminals, and unfortunately that equates to significant losses for businesses”
said Vice President at IBM X-Force Threat Intelligence, Wendi Whitmore.
“With organisations facing the loss or theft of over 11.7 billion records in the past 3 years alone, companies need to be aware of the full financial impact that a data breach can have on their bottom line – and focus on how they can reduce these costs.”
Cybersecurity by the Numbers
As reported by Varonis, cybersecurity issues are becoming a day-to-day struggle for businesses and their IT departments, with current trends showing huge increases in hacked and breached data from workplace sources.
In addition, further research from Varonis suggests that the majority of companies operating today have poor cybersecurity practices in place, leaving sensitive data unprotected and exposed to cybercriminals.
These attackers look for unsecured folders as soon as they gain access to a company’s network. Folders open to global access groups – such as domain users or authenticated users – provide attackers with easy access to things like business plans, intellectual property, customer and employee data, credit card information, and more besides.
As the report’s authors note: “Globally, accessible data puts organisations at risk from malware and ransomware attacks: it takes just one click on a phishing email to set off a chain reaction that encrypts or destroys all accessible files.”
(Image source: info.varonis.com)
Hacker Methodology – The Cyber Kill Chain
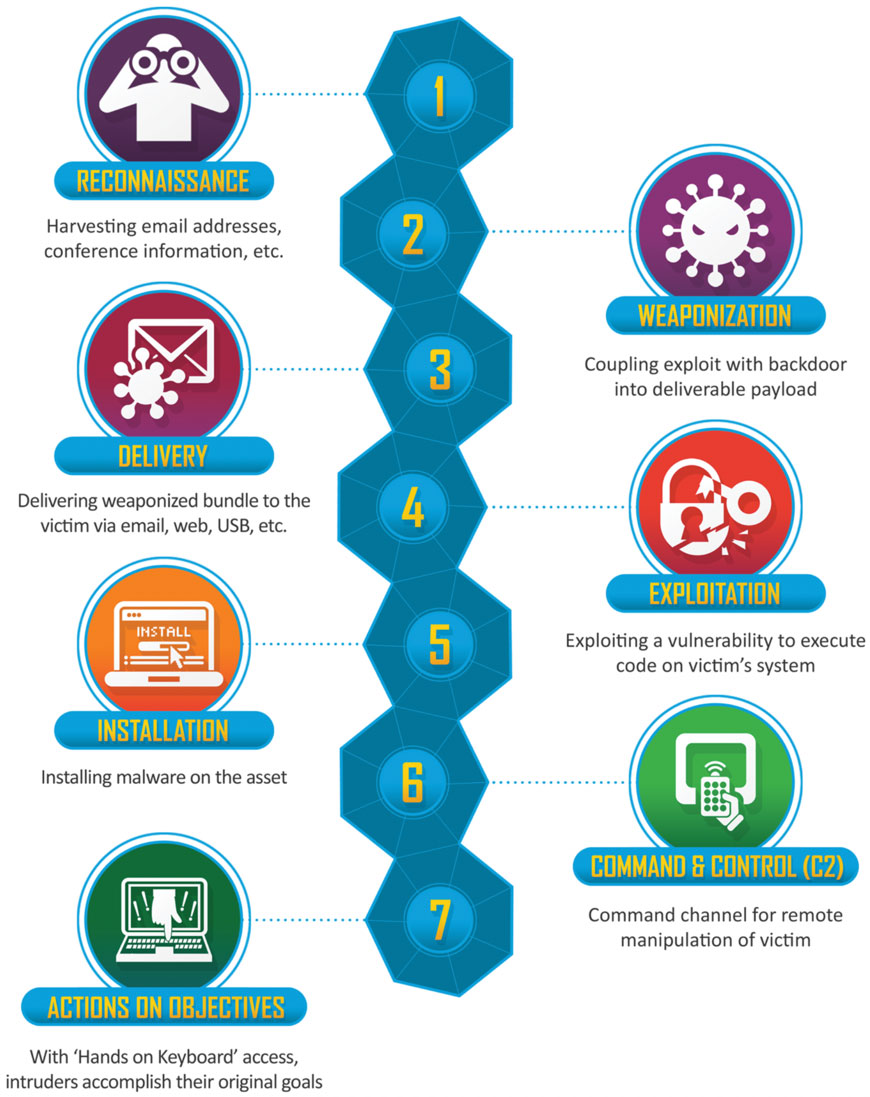
How do cybercriminals infiltrate a business’s network to steal data? Well, hackers typically employ a certain methodology known as the Cyber Kill Chain, developed by Lockheed Martin Corp.
The Cyber Kill Chain consists of seven stages:
- Reconnaissance (identify targets): The attacker assesses targets remotely, identifying vulnerabilities in information systems to exploit.
- Weaponization (prepare attack): The attacker creates malware customised to exploit the vulnerabilities discovered in the reconnaissance stage.
- Delivery (launch attack): The attacker sends the malware to the target, often by a phishing email or man-in-the-middle attack.
- Exploitation (gain access): The attacker now exploits a vulnerability to gain access to the company’s network.
- Installation (establish beachhead): Once the attacker has infiltrated the company network, a persistent backdoor or implant is installed to maintain extended access.
- Command and Control (remote control of the implant): The installed malware now opens a command channel, enabling the attacker to take over the control of the target’s systems and devices.
- Actions on Objectives (accomplish goals): The attacker can now carry out his/her mission, which may be to steal or corrupt data, destroy the system, demand a ransom, or anything else.
(Image source: lockheedmartin.com)
Network Security
With cybercriminals becoming ever-more sophisticated in their attack methods – and the cost of data breaches getting higher and higher – robust IT network security is of paramount importance to the organisation.
Network security is about defining and designing a set of rules and configurations to protect the integrity, confidentiality and accessibility of a company’s IT networks and data using both hardware and software technologies. Well-configured network security allows authorised users to gain access to the network, while malicious actors are blocked.
However, there are many, many layers to consider when addressing network security across an organisation, including physical, data link, network, transport, session and application. Attacks can happen at any layer, meaning both hardware and software must be adequately secured around the clock.
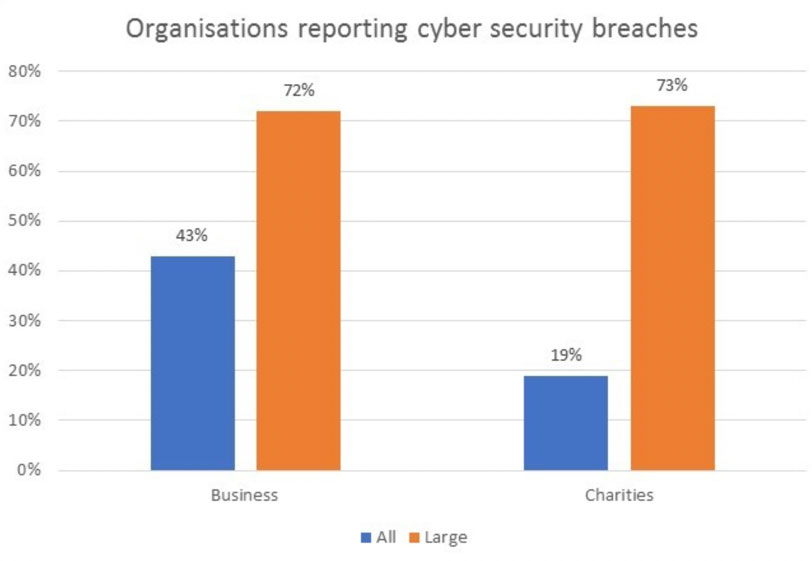
It’s hardly surprising, therefore, that breaches are common occurrences. According to figures from ICAS published in November 2018, 43% of UK small businesses 72% of large enterprises had suffered cybersecurity breaches over the previous twelve months, along with 19% of small and 73% of large UK charities.
(Image source: icas.com)
Securing networks takes time and resources – and time and resources cost.
According to the ICAS study, the cybersecurity breaches suffered by organisations result in extra staff time being needed to deal with the disruption.
In addition, staff are then unable to carry out their normal duties, and later need to devote even more resources to bolster defences against future attacks.
This is time that businesses can’t afford – and precisely where utilising the expertise and resources of managed technology services providers can be of invaluable benefit.
Improving Security with Managed Technology Services
Managed technology services providers diligently keep all of your IT systems secure from the ever-looming threat of cyberattacks.
From patch management to vulnerability scanning, risk assessing, updating, reporting, disaster recovery and data backup, managed technology services providers bring round-the-clock industry-best security practices and procedures to your organisation.
Dedicated service consultants conduct regular reviews of your systems, networks and technologies to constantly monitor for security threats in order to mitigate risk and manage recovery in the event of a breach.
In addition, a managed technology services provider’s data centres and managed network infrastructure will be much more robust than most standard enterprise IT setups. Run under 24/7/365 management, you can be sure your organisation’s data is protected using industry-leading technology, practices and procedures.
This all means that your organisation will not only benefit from having the robust security measures in place that are required to protect your business against modern cyberattacks, but your internal IT staff will be freed from the constant burden of managing cybersecurity, allowing them to dedicate their time to projects that further your core business objectives and promote innovation.
Managed Technology Services from zsah
Businesses have limited resources, and where time equals money, maximising those resources while lowering costs is key to remaining productive and competitive. Organisations that try to conduct all their IT services in-house suffer huge drains on time, resources and salaries – all of which increase costs that ultimately get passed on to customers.
With managed technology services from zsah, you will benefit from decreasing service and employee downtime, and robust network and data protection from our ISO accredited solutions, 24/7 risk monitoring, unrivalled security expertise and high-security data centres. This is all overseen by dedicated account managers and engineers who are committed to looking after your business’s core IT requirements on a personal level.
Whether your infrastructure is hosted, on-premise or cloud-based, we work around the clock to ensure everything is configured, highly secure, and performing to its optimum.
At Zsah, we understand that most businesses want and need to be able to focus on their core processes without having to jump over IT-related hurdles. With our managed technology services, you no longer have to devote time and manpower to managing your own infrastructure, applications, and all the security provisions that come with them.
As a truly managed service, we pride ourselves on working hand in hand with our clients. This means that we take the time to fully understand and provide solutions that are designed perfectly to suit your organisation – and once those solutions are in place, our highly-specialised UK-based support team are accessible 24 hours a day, seven days a week.
Get in touch today to find out more about how our managed technology services solutions can unleash new growth potential for your business.
Want to save a PDF version of this post?
Just enter your email below and we'll send you a copy.